Block XML-RPC with Apache mod_rewrite module
WHAT IS XML-RPC 🤔
According to Kevin Wood 
XML-RPC is a feature of WordPress that enables data to be transmitted, with HTTP acting as the transport mechanism and XML as the encoding mechanism. Since WordPress isn’t a self-enclosed system and occasionally needs to communicate with other systems, this was sought to handle that job.
For example, let’s say you wanted to post to your site from your mobile device since your computer was nowhere nearby. You could use the remote access feature enabled by xmlrpc.php to do just that.
The core features that xmlrpc.php enabled were allowing you to connect to your site via smartphone, implementing trackbacks and pingbacks from other sites, and some functions associated with the Jetpack plugin.The biggest issues with XML-RPC are the security concerns that arise. The issues aren’t with XML-RPC directly, but instead how the file can be used to enable a brute force attack on your site.
Sure, you can protect yourself with incredibly strong passwords, and WordPress security plugins. But, the best mode of protection is to simply disable it.
Let’s Block It With Apache mod_rewrite🧐
Step 1 – Go to your wordpress folder (should be in “xampphtdocswordpress” by default)
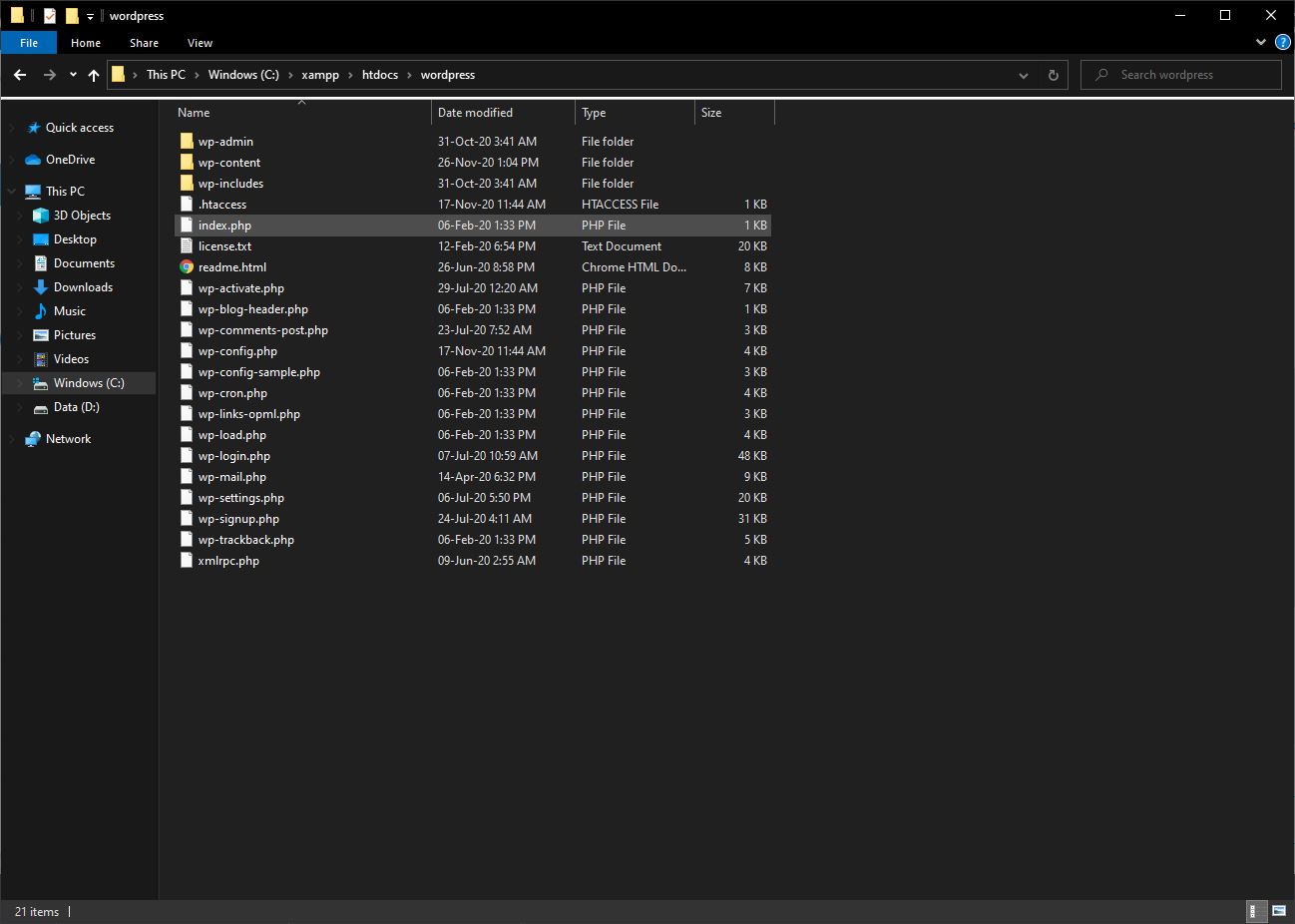
Step 2 – Open “.htaccess” file with your prefer code editor
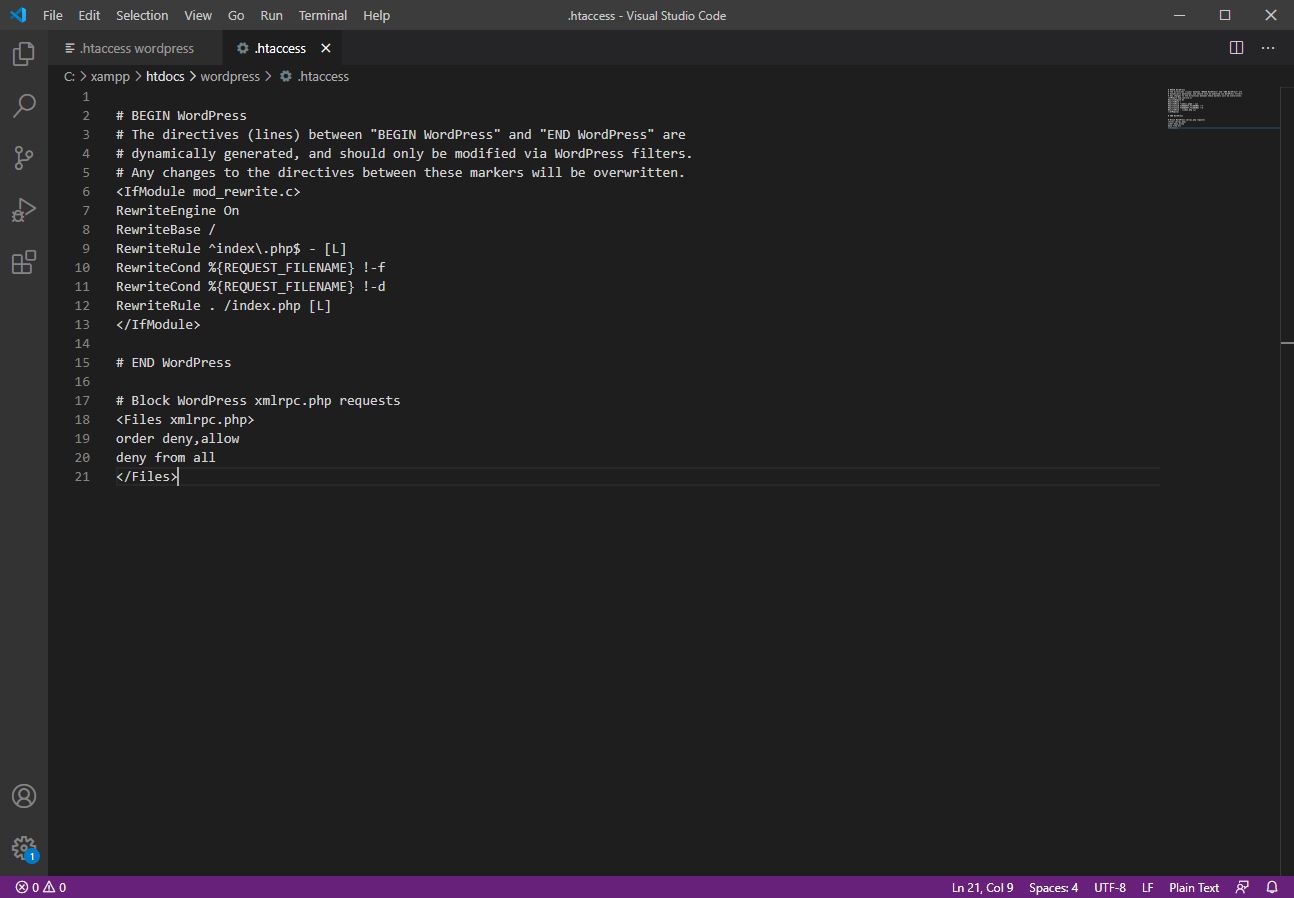
Step 3 – Add following code after “# END WordPress” and Save the file
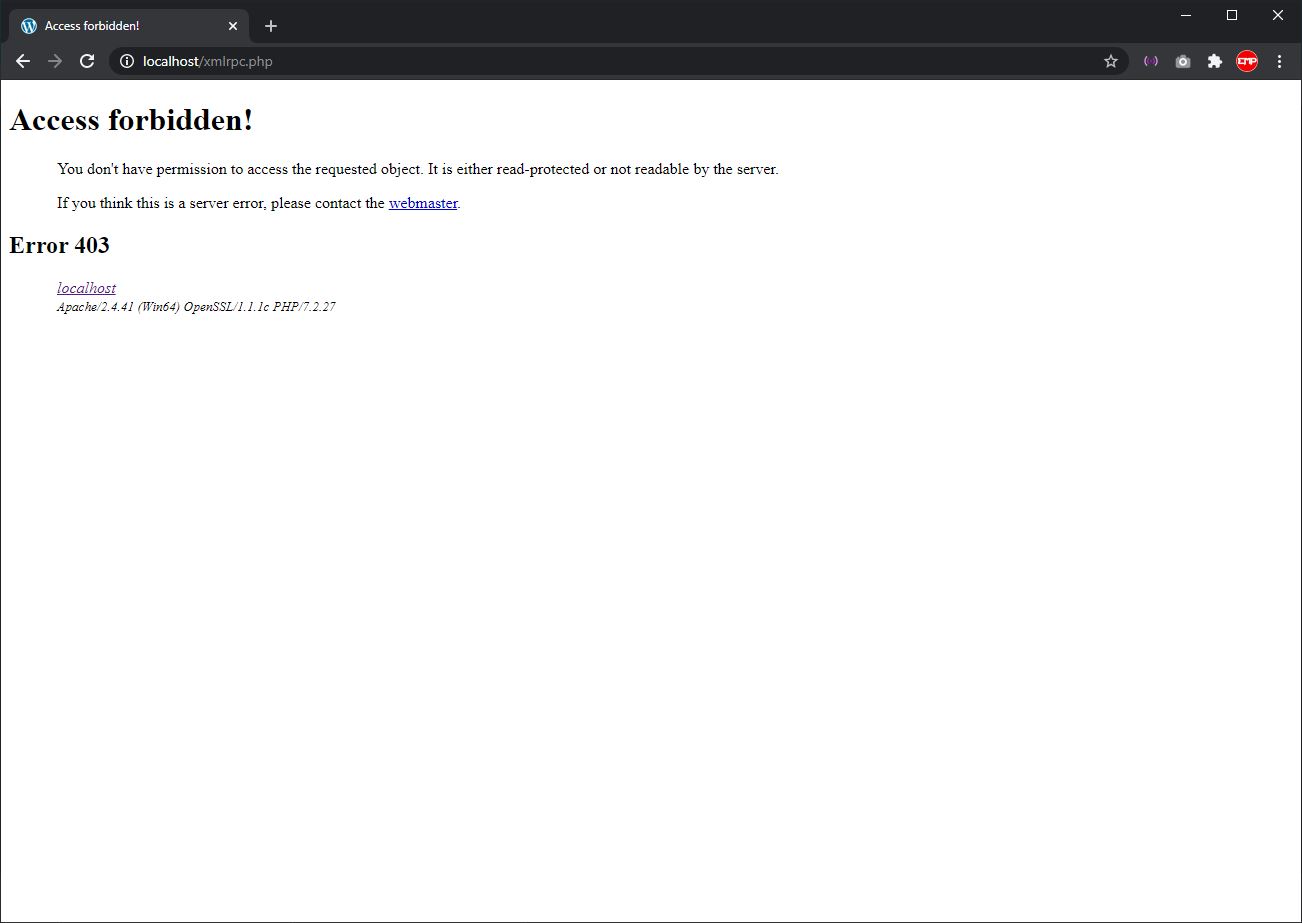
Step 4 – Go to “<your wordpress website>/xmlrpc.php” and check if it has been block.





Leave A Comment